I'm slow on the uptake sometimes. So today I decided to pick a 'thread' and follow its ongoing unwinding ...
That 'thread' I chose to unravel, is this high-powered Internet data sniffer, sorter and collator (now a subsidiary of Boeing) -- the Narus STA 6400.
And here is the clip that initially sparked my interest ... Frontline, I like Frontline. They still do Journalism, the way it used to be done ...
What are they trying to tell me now a few years ago ...
Breaking the Story
NOW, pbs.org -- 2.16.07
[...]
NOW: What would you say is the most significant thing or things that these documents reveal?
[Journalist Ryan] Singel: What the documents reveal is that there's a room in the AT&T switching center in San Francisco. And that inside there's a big machine made by this company NARUS -- it is used for analyzing data traffic, or for complying with wiretapping orders. What was really interesting was that what was going into this room was not simply AT&T's traffic. The way the Internet works is that AT&T's network needs to be connected up with other people's network so they can exchange traffic. So if you have an EarthLink email account and I have an AT&T WorldNet account and I want to email you, the data has to somehow transfer. So the way that works is that AT&T's network and EarthLink often have a connection. And the connections from those other ISPs -- portions of that fiber optic signal were then sliced off and sent into this room. Having the names, dates, and size of the connections really added weight to Klein's belief that this room was intended for some sort of eavesdropping.
Is the NSA reading your e-mail? pbs.org FRONTLINE
link to clip
Uploaded on May 9, 2007
About the Frontline clip:
Former AT&T technician Mark Klein and internet expert Brian Reid describe an NSA listening room that Klein discovered while working at the company's operations center. In "Spying on the Home Front" FRONTLINE talks to intelligence insiders and asks: Is the Bush administration's domestic war on terrorism jeopardizing our civil liberties?
Coming May 15 [2007] to PBS and online at www.pbs.org/frontline/homefront [...]
My partial transcript of the Frontline clip:
Mark Klien (Former AT&T Technician): But then there was one thing that was odd -- because I did not recognize it. It was not part of normal day to day telecommunications equipment that I was familiar with. And that was a Narus -- n-a-r-u-s -- Narus STA 6400.
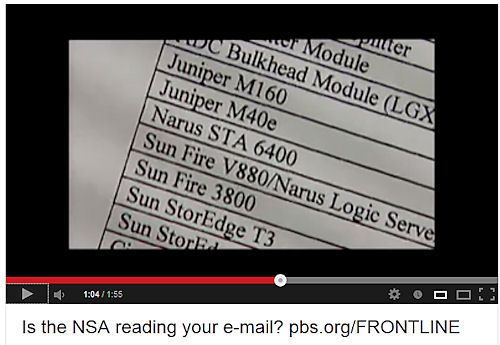
Brian Reid (Internet Expert): The Narus STA 6400 made me sit up and take notice, and realize this was not an amateur game. And so when you see a Narus box and all that storage space and all that computing power -- you can't help but think: 'WOW, this is some heavy-duty processing here to really analyze the data that is siphoned off. WHAT IS going on?'
"Spying on the Home Front" -- FRONTLINE, May 15, 2007
Introduction
[...]
The watershed, officials tell FRONTLINE, was the government's shift after 9/11 to a strategy of pre-emption at home -- not just prosecuting terrorists for breaking the law, but trying to find and stop them before they strike.
[...]
Peter Swire, a law professor and former White House privacy adviser to President Clinton, tells FRONTLINE that since 9/11 the government has been moving away from the traditional legal standard of investigations based on individual suspicion to generalized suspicion. The new standard, Swire says, is: "Check everybody. Everybody is a suspect."
Ahh, but,
'I haven't done anything wrong!'
There was a historical context to this ramp-up of using the Narus System, to keep tabs on ALL corners of the internet.
Enter stage right, G.W. Bush and his Preemptive Strike doctrine. Terror is everywhere ... don't you know?
Bush: Secret wiretaps have disrupted potential attacks
President says speed of eavesdropping essential
CNN.com -- December 20, 2005
[...]
"We know that a two-minute phone conversation between somebody linked to al Qaeda here and an operative overseas could lead directly to the loss of thousands of lives," Bush said. "To save American lives, we must be able to act fast and to detect these conversations so we can prevent new attacks." (Watch Bush defend use of wiretaps -- 2:23 [deleted link])
"It has been effective in disrupting the enemy while safeguarding our civil liberties," the president added.
But lawmakers, several of whom said Congress hadn't been informed about the wiretap program, also are concerned about the legality of the president's authorization.
Democratic Sen. Russ Feingold of Wisconsin told CNN on Sunday that he believes Bush's action violated the law.
'There Is Oversight. We're Talking to Congress All the Time'
EXCERPTS FROM PRESIDENT BUSH'S NEWS CONFERENCE
LATimes.com, From Associated Press -- December 20, 2005
[...]
Q.: I wonder if you can tell us today, sir, what, if any, limits you believe there are or should be on the powers of a president during wartime. And if the global war on terror is going to last for decades, as has been forecast, does that mean that we're going to see, therefore, a more or less permanent expansion of the unchecked power of the executive in American society?
Bush: First of all, I disagree with your assertion of unchecked power. There is the check of people being sworn to uphold the law, for starters.
There is oversight. We're talking to Congress all the time.... This is an awesome responsibility to make decisions on behalf of the American people. And I understand that. And we'll continue to work with the Congress, as well as people within our own administration, to constantly monitor a program such as the one I described to you to make sure that we're protecting the civil liberties of the United States.
To say "unchecked power" basically is ascribing some kind of dictatorial position to the president, which I strongly reject.
Transcript: President Bush's Press Conference: 12/19/2005
[...]
Let's see here -- Martha [Martha Raddatz, ABC News] -- working my way around the electronic media, here.
Domestic Wiretaps
Q. Thank you, Mr. President. You say you have an obligation to protect us. Then why not monitor those calls between Houston and L.A.? If the threat is so great, and you use the same logic, why not monitor those calls? Americans thought they weren't being spied on in calls overseas -- why not within the country, if the threat is so great?
The President. We will, under current law, if we have to. We will monitor those calls. And that's why there is a FISA law. We will apply for the right to do so. And there's a difference -- let me finish -- there is a difference between detecting, so we can prevent, and monitoring. And it's important to know the distinction between the two.
Q. But preventing is one thing, and you said the FISA laws essentially don't work because of the speed in monitoring calls overseas.
The President. I said we use the FISA courts to monitor calls. It's a very important tool, and we do use it. I just want to make sure we've got all tools at our disposal. This is an enemy which is quick, and it's lethal. And sometimes we have to move very, very quickly. But if there is a need based upon evidence, we will take that evidence to a court in order to be able to monitor calls within the United States.
Speaking of "all the tools" and quickly "
detecting the trouble" before it starts ... enter the deep-detection service-provider Narus. When there is a deep-data need,
there will be a deep-pockets way ...
NARUS, deep packet inspection and the NSA
privacysos.org
Narus, the STA 6400 and AT&T
[...]
Almost a year later, Bamford reports, Klein was transferred to the Folsom street facility,
where he was put in charge of the WorldNet Internet room, one floor above the secret NSA room. "As soon as I saw the splitter," Klein said, "I knew this was completely unconstitutional and illegal because they were copying everything. I'm a technician, I know what this equipment does, and I traced the cable. This cable goes to that room, which we can't go into; that's a government room. And I knew what was on that cable...It was everything that went across the Internet then, which was Web browsing and email, and VoIP calls...Based on my understanding of the connections and equipment at issue...it appears the NSA is capable of conducting what amounts to vacuum-cleaner surveillance of all the data crossing the Internet...The physical apparatus gives them everything."
The "physical apparatus" Klein describes was a Narus system. The key part of the system, Klein discovered, was a 'Narus STA 6400,' a 'Semantic Traffic Analyzer.' Another piece of Narus equipment was also in that room: the Narus Logic Server. As Bamford aptly summarizes, these technologies were initially developed so that internet companies could break down internet activity into "packets," allowing for telecoms to appropriately charge consumers for their bandwith usage. But soon after the attacks on 9/11, Narus realized it could market the technologies to governments for wide-ranging surveillance. And it did just that.
[...]
If you are interested to learn about how Narus super computers can be used for nefarious purposes, watch the video below. It describes how the Egyptian government used the product to crack-down on protest leaders during the 2011 revolution against Mubarak in that country.
Egypt's cyber-crackdown aided by US company
link to video
AlJazeeraEnglish -- Uploaded on Feb 5, 2011
What these super-sniffers can do,
is no joke -- when used by secret agencies, with next to no public oversight, and
very loose definitions of 'exactly who the enemy is.' ... Just listen to that short clip, or read about the 'dissenter roundups' in the next link, to see
just WHAT Narus can do, especially when constitutions no longer serve to protect their citizens; you know,
in times of endless wars, and other such 'civil emergencies' ...
One U.S. Corporation's Role in Egypt's Brutal Crackdown
by Timothy Karr, Free Press and SavetheInternet.com, Huffingtonpost.com -- 01/28/11
The open Internet's role in popular uprising is now undisputed. Look no further than Egypt, where the Mubarak regime today reportedly shut down Internet and cell phone communications -- a troubling predictor of the fierce crackdown that has followed.
What's even more troubling is news that one American company is aiding Egypt's harsh response through sales of technology that makes this repression possible.
The Internet's favorite offspring -- Twitter, Facebook and YouTube -- are now heralded on CNN, BBC and Fox News as flag-bearers for a new era of citizen journalism and activism. (More and more these same news organizations have abandoned their own, more traditional means of newsgathering to troll social media for breaking information.)
But the open Internet's power cuts both ways: The tools that connect, organize and empower protesters can also be used to hunt them down.
[...]
'Trouble-makers' are in the eye of the beholder. In the data heaps too, of Narus-solution owners.
What these super-sniffers can do, with the off-the-shelf Narus software is startling enough. There's no telling what it may end up doing, when those Narus customers (from around the world) pay to get the software developer kit, which empowers them to build-their-own individually unique, state-security 'solutions' ...
The Ultimate Net Monitoring Tool
by Robert Poe wired.com/science -- 05.17.06
[...]
Narus' product, the Semantic Traffic Analyzer, is a software application that runs on standard IBM or Dell servers using the Linux operating system. It's renowned within certain circles for its ability to inspect traffic in real time on high-bandwidth pipes, identifying packets of interest as they race by at up to 10 Gbps.
Internet companies can install the analyzers at every entrance and exit point of their networks, at their "cores" or centers, or both. The analyzers communicate with centralized "logic servers" running specialized applications. The combination can keep track of, analyze and record nearly every form of internet communication, whether e-mail, instant message, video streams or VOIP phone calls that cross the network.
[...]
That legal eavesdropping application was launched in February 2005, well after whistle-blower Klein allegedly learned that AT&T was installing Narus boxes in secure, NSA-controlled rooms in switching centers around the country. But that doesn't mean the government couldn't write its own code to do the dirty work. Narus even offers software-development kits to customers.
"Our product is designed to comply (with) all of the laws in all of the countries we ship to," says Bannerman [from Narus]. "Many of our customers have built their own applications. We have no idea what they do."
[...]
Ahh, talk about 'aiding and abetting the enemy' ...
Fast forward to 2013, Narus.com is still selling its updated wares to the brave new unsuspecting interwebbed world ... certain corners of it anyways (like Telecom Egypt and other state authorities, and major telecoms).
Incisive Intelligence
Visibility, context and control are the keys to cybersecurity in our dynamic, hyperconnected world.
Enter Cyber 3.0: harnessing the principles of the semantic web for automated machine learning that lets you act faster and proactively defend against emerging cyberthreats. Learn more Cyber 3.0 infographic (pdf's)
Cue the NARUS promotional cyber-blurb (circa 2013):
As the Internet grows more complex and dynamic, information security organizations face enormous volumes of data, users connected at tremendous speeds, and ever-changing dynamics with new devices and applications entering the network all the time.
The only way for organizations to stay ahead is to perform cyber intelligence analysis on every piece of data that flows across the network. And, they must understand that data in context of everything else that is happening in the world. This level of cyber security analysis is impossible for any human or team of humans to undertake. That is why the future of cybersecurity requires a new approach: drawing from the richly layered semantic web to enable machine-to-machine analysis and automated machine learning to bring deep new meaning to network activity and behavior.
[...]
Afterall, how else will they
ever keep up, with all this people-powered social progress, without a lot of help from their NARUS cybersecure, data-mining friends?
Because actually stopping to talk to people, is WAY too much trouble -- don't you know? ... especially when you do your 'best work' from deep within the shadows.


